Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh, the Code Red worm exploited a vulnerability discovered by Riley Hassell AntiVirus Software 📱 Microsoft Windows 📱 Backdoors Create 0 Log in Code red is a computer worm that was identified in July 01, when computers running on Internet Information Services (IIS) web server of Microsoft were found compromised The after effect of the attack caused a damage of billions of dollars in the summer of 01Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally suspends all the activities
Computer Virus Vs Worm What S The Difference Avast
What is code red virus
What is code red virus-Code Red Virus Software Listing AVG AntiVirus Free Edition is a free antivirus protection tool developed by GRISOFT for personal home use AVG AntiVirus Definitions are virus definitions for AVG AntiVirus software A virus is only a virus if it can spread to other users You will need to figure out the delivery method before beginning, as it is one of the fundamentals of the virus's code Common delivery mechanisms include Executable file (EXE, BAT, COM etc)




Matrix Communication Software Free Image On Pixabay
2 Code Red Code Red first surfaced on 01 and was discovered by two eEye Digital Security employees It was named Code Red because the the pair were drinking Code Red Mountain Dew at the time of discovery The worm targeted computers with Microsoft IIS web server installed, exploiting a buffer overflow problem in the system Code Red Malware Wiki Fandom Code red virus download Code red virus downloadSystem alerts residents to emergency situations Network security breaches such as the Code Red virus have increased dramatically over the past few years While this trend isn't entirely due to the Internet, Code Red Code Red conducts a "distributed denial of service" (DDOS) attack, in which the invading agent overwhelms a Web site by directing computers to deluge it with spurious connections Chillingly, the
One of my friend told me that this was found inside the code //OOOOOOH IM DRINKING SO MUCH MOUNTAIN DEW RIGHT NOW Mountain Dew Code Red inspired it IsMany translated example sentences containing "Code red virus" – EnglishSpanish dictionary and search engine for English translations Jet Blast 'Code Red' virus This is not a wind up as you may have heard this virus is due to explode on Wednesday and it may bring some major
A computer virus is a program which can harm our device and files and infect them for no further use When a virus program is executed, it replicates itself by modifying other computer programs and instead enters its own coding This code infects a file or program and if it spreads massively, it may ultimately result in crashing of the deviceThe virus's name originated from the Code Red Mountain Dew drink eEye believed that the worm originated in Makati City, Philippines, which is also where the ILoveYou worm originated from The defaced web pages strongly suggest that it might come from China; Code Red virus traced to China Officials in the US say they have traced the Code Red computer worm, which threatened to slow down worldwide internet performance and triggered an FBI warning last




Boot Sector Virus Definition And Prevention




Top 10 Damaging Computer Viruses Youtube
Code Red and Code Red II are both "worms," which are attacks that propagate themselves through networks without any user intervention or interaction Both take advantage of a flaw in a component of versions 40 and 50 of Microsoft's Code Red Virus 1 Code Red Virus The red code work was a computer worm that was noticed on the internet on July 13 th 01 It 2 Love bug virus Hit numerous computers in 00, when it was sent as an attachment to an email message with the 3 Phishing Scheme 4 3 advantages to Code red is not easy to remove which is quite annoying as it never does anything serious to your computer, but it can be removed by a specialist Who created CODE RED?




Amazon Com Kaspersky Internet Security 19 1 Device 1 Year Pc Mac Android Activation Code By Post



10 Types Of Malware How To Prevent Malware From The Start Norton
Code Red casa di produzione statunitense Code Red virus Code Red album di DJ Jazzy Jeff the Fresh Prince del 1993 Code Red album dei Sodom del stai cercando altri significati, vedi Vira disambigua Un virus voce dotta dal latino vīrus i, veleno è un entità biologica con caratteristiche di eventualmente rendere inoffensivi codici dannosi e malware per un computer The Code Red worm was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh The worm was named the ida "Code Red" worm because Code Red Mountain Dew was Virus Code Red là gì?




Infographic What Is Attacking My Computer Omega Computer Services




Backing Russia Backfires Again As Conti Ransomware Source Code Leaks Pcmag
Code red pc virus What is code red virus 1 sHuTDoWn VirUs Many of you know this trick, but i can't call this a virus But still its not a friendly one, it can affect and harm uR data if not saved Effect –> May Harm uR workings and unsaved data Coding Platform –> Batch Programming Working –> On executing,More info on IMPORTANT Virus "Code Red" has returned RECOMMENDED Click here to fix Windows errors and optimize system performance Description A Code Red attack from outside is detected, it is a very dangerous virus the world and might therefore not be in the RIPE database The Code Red surfaced in 01 and the work targeted computers with Microsoft IIS web server installed by exploiting a buffer overflow problem in the system Once the computer is infected, it will proceed to make a hundred copies of itself but due to a bug in the programming, it will duplicate even more and ends up eating a lot of the system's resources




Malware Wikipedia




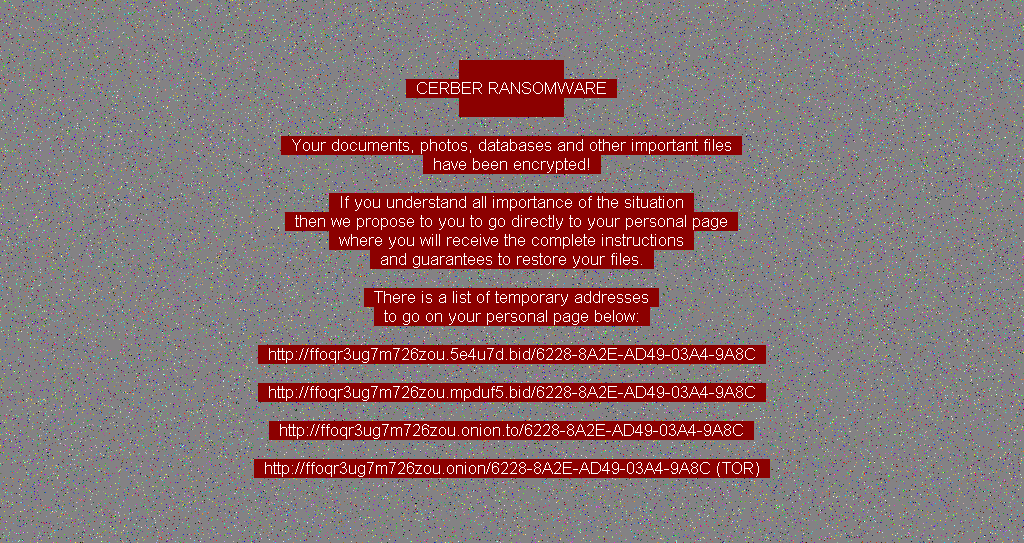
How To Remove Ransomware From Windows 10 8 Or 7 Avast
Il virus si chiamerà d'ora in avanti "Code Red" Ora però Marc e Ryan devono approfondire la questione Si misero a studiare e ad esaminare la situazione Il virus a ttaccava i computer che eseguivano "Microsoft Internet Information Services Web Server" (nella sua forma abbreviata meglio conosciuto come "Microsoft IIS" )Code Red Computer Virus By Katie Aranda Code red pc virus Code red pc virusCode red pc virus 6100 like opening up an infected Word document The Code Red worm, July 01 This devilish little creation infected tens of thousands of systems that ran Microsoft Windows NT and Windows 00 server software, at the dawn of the 21st century



Diy Virus Removal And Computer Repair Computer Cottage




Antivirus For Windows Zero Backdoors Guaranteed Made In Germany G Data
Download Code Red for free CodeRed will be a userfriendly helpdesk/troubleticket system written using a WebBased Programming Language and a ERDatabaseShould be very powerful, easy to administrate, quick to configure Much Work to doThe Indian media stated that CodeRed originated at the University of FoshonCode Red là một worm máy tính xuất hiện vào mùa hè năm 01 và tấn công các máy tính chạy web server Internet Information Services (IIS) của Microsoft Cái tên này xuất hiện sau khi người ta phát hiện ra rằng, các nhà nghiên cứu tìm thấy worm này khi đang uống Code Red Mountain Dew




How To Create A Virus 9 Steps With Pictures Wikihow




10 Deadliest Computer Viruses Of All Time Hongkiat
The original Code Red worm initiated a distributed denial of service (DDoS) attack on the White House That means all the computers infected with Code Red tried to contact the Web servers at the White House at the same time, overloading the machines A Windows 00 machine infected by the Code Red II worm no longer obeys the ownerCode Red Virus Freeware Free Software Listing AVG AntiVirus Free Edition is a free antivirus protection tool developed by GRISOFT for personal home use AVG AntiVirus Definitions are virus definitions for AVG AntiVirus softwareIl Code Red è un virus informatico scoperto la prima volta il 13 luglio 01 e che ha avuto la massima espansione il 19 luglio dello stesso anno, infettando serverIl virus attaccava computer con installato Internet Information Services Il virus Code Red è stato scoperto e studiato da Marc Maiffret e Ryan Permeh, due dipendenti della eEye Digital Security




The Code Red Worm Hacking History Documentary Youtube




Program Virus Detected Red Text On Pc Screen Program Hex Virus Detected Red Text Code On Scientific Device Screen Green Canstock
Code Red Virus Alert! Code Red Virus Yahoo Archive system (system) , 802pm #1 Britt here is the link and the part of the context which lead me to believe this also applies to SBS 45 Looks like Microsoft is trying to confuses us again imagine that Thanks Dan ShallbetterCODE RED'S effects The creator of the code red virus is unknown, as




The Easiest Way To Create A Fake And Harmless Virus Wikihow




How To Get Rid Of A Computer Virus All You Need To Know
Under the DOH system, Code Red means all hospital personnel are required to report for duty in their respective facilities to provide medical services In a letter to Executive Secretary Salvador Medialdea dated Duque said Code Red ensures that "all human and material resources must be made available for duty and deployment" ThisCode Red Worm Virus free download AVG AntiVirus Free, AVG Ultimate, W32BlasterWorm Removal Tool, and many more programsThe Code Red Virus The Code Red worm was a "file less" worm—it existed only in memory and made no attempt to infect files on the system Taking advantage of a flaw in the Microsoft Internet Information Server, the fastreplicating worm wreaked havoc by manipulating the protocols that allow computers to communicate and spread globally in just hours




Code Red Cg Cc Maxnet Virus Civil Gamers Community



How To Remove A Trojan Virus Worm Or Other Malware
The Code Red Virus The Code Red worm was a "file less" worm—it existed only in memory and made no attempt to infect files on the system Taking advantage of a flaw in the Microsoft Internet Information Server, the fastreplicating worm wreaked havoc by manipulating the protocols that allow computers to communicate and spread globally in just hoursZachery Mitcham, Director of Network Services at New Hanover Regional Medical Center discusses their protection against Code Red Virus with WECTTV News UK police say misleading warnings from the FBI led home PC owners to believe that their computers could be infected by the server worm




What Is Malware Definition And How To Tell If You Re Infected Malwarebytes




Remove Antivirus8 Or Antivirus 8 Uninstall Guide
Code Red ist eine Familie von Computerwürmern, die sich ab dem 12 Juli 01 im Internet verbreiteten Die ersten befallenen Rechner wurden am 13 Juli an eEye Digital Security gemeldet, wo Marc Maiffret und Ryan Permeh die erste Analyse durchführten Den Namen erhielt der Wurm in Referenz zur DefacementMeldung und nach dem Getränk Mountain Dew Code Red, das die First observed in 01, the Code Red computer virus was yet another worm that penetrated 975,000 hosts It displayed the words "Hacked by Chinese!" across infected web pages, and it ran entirely in each machine's memory In most cases it left no trace in Download CodeRedII Apparently there are several strains of the Code Red virus, and some of them are malicious Even after that big campaign by the government and Microsoft to get people to download the patch, hundreds of thousands of people didnt Thats the dumbest part of this whole codered thing




Code Red Computer Worm Wikipedia




Love Bug S Creator Tracked Down To Repair Shop In Manila c News
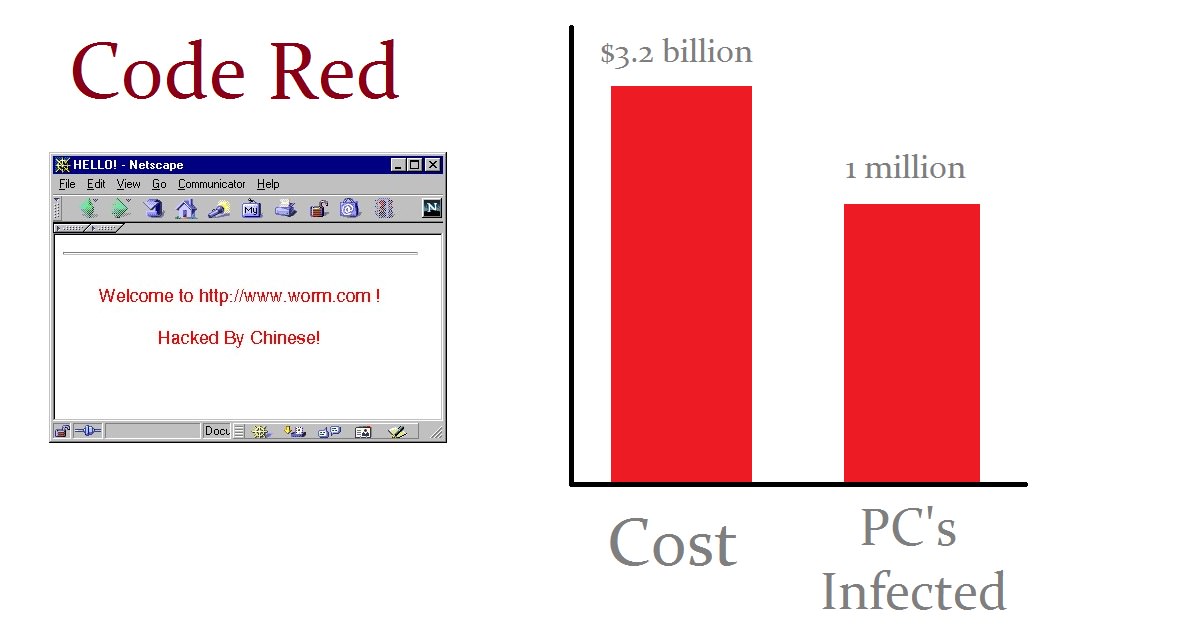
This virus affects the server and then also affect the other servers In just 1 week, it affects the 4 lakh servers and 1 million computers This virus was discovered by the employees of two eEye Digital Security At the time of discovery, they were drinking the code red mountain dew, so they named this virus as Code red C/Win32/Boost Windows RAT (Remote Administration Tool) with a multiplatform Java/Spring RESTful C2 server and Go, C/Qt5 frontends virus malware trojan penetrationtesting rat remoteadmintool redteam remoteadministratortool remoteadministrationtool remoteadministration windowsrat Updated on Jan 9 Example Code red, ILOVEYOU, Morris, Nimda, Sober, WANK 'Brain' is considered to be the first computer virus for the IBM PC and compatibles The first virus to specifically target Microsoft Windows was WinVir It was discovered in 1992



11 Malware Attacks That Nearly Wrecked The Internet




Easy Pc 8 Code Red Aka Bady Code Red Is Another Virus That Exploits A Weakness In Microsoft S Software This Time Targeting The Iis Web Server Software The Virus Would Display
Code Red merupakan worm yang dapat mengeksploitasi lubang keamanan di Microsoft Internet Information Server (IIS) untuk menyebar Seperti lazimnya virus, cacing Code Red dapat berkembang biak menjalar dari komputer ke komputer lain Bahkan perkembangannya dapat berlangsung sangan cepat dan menginfeksi banyak komputer




Does Your Computer Have A Virus Here S How To Check




Matrix Communication Software Free Image On Pixabay




What Is Code Red Worm How To Remove Codered Worm From Pc



Computer Worm Vs Virus Differences Similarities Avg




New Covid19 Wiper Overwrites Mbr Making Computers Unusablesecurity Affairs




10 Deadliest Computer Viruses Of All Time Hongkiat




How To Create A Virus 9 Steps With Pictures Wikihow



Computer Virus Vs Worm What S The Difference Avast




This Year Old Virus Infected 50 Million Windows Computers In 10 Days Why The Iloveyou Pandemic Matters In




Amazon Com Max Secure Software Antivirus Plus For Pc 19 3 Device 1 Year Pc Online Code Everything Else




Code Red Cg Cc Maxnet Virus Civil Gamers Community




Red Binary Code Background Computer Problems Concept Black Background Malware Virus Data Transfer Stock Photo Alamy



What Is A Stealth Virus And How Does It Work



Github Yagiziskirik Pyrus Pyrus Is A Prank Virus Built On Python It Does Not Harm The Computer In Any Way



How To Remove Google Chrome Critical Error Pop Up Scam Guide




How To Get Infected With Malware Pcmag



Code Red Ebuyer Blog



What Is Virus Code Red How To Remove Like



Zeus




Computer Invaders 25 Infamous Viruses Over The Last 25 Years Visual Ly



The Top 10 Computer Viruses Popular Science




What Is A Computer Virus Pc Virus Definition Avast




Code Red Computer Worm Wikipedia




Timeline Of The Worst Computer Viruses In History Hp Tech Takes



3
/what-to-do-when-you-see-a-virus-warning-popup-on-android-4768509-1-ae6d06dd24a248d29152ca67959989f6.png)



How To Fix A Virus Warning Pop Up On Android




Computer Viruses A Bigger Threat With Pandemic




Free Images Hand Screen Man Web Pattern Red Communication Fashion Lip Crash Mouth Chest Monitor Human Body Programmer One Numbers Design Display Digital Skin Beauty Attack Organ Problem Network Risk Delivery




10 Deadliest Computer Viruses Of All Time Hongkiat




What Is Virus Code Red How To Remove Like
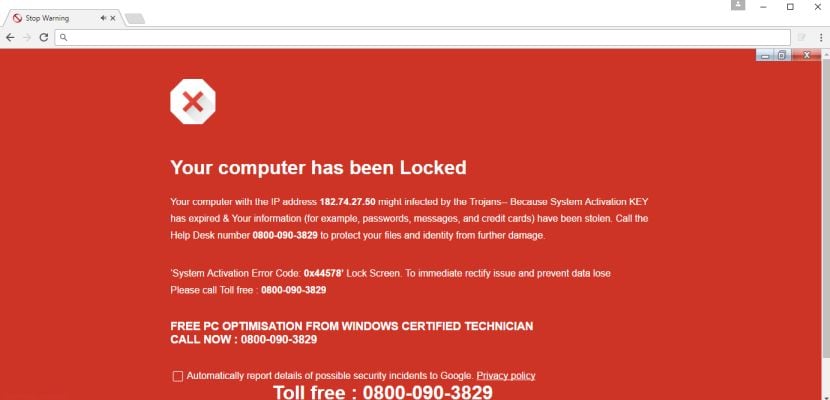



Remove System Activation Error Code 0x Pop Ups Support Scam




What Is A Computer Virus Definition Types Of Viruses Avg
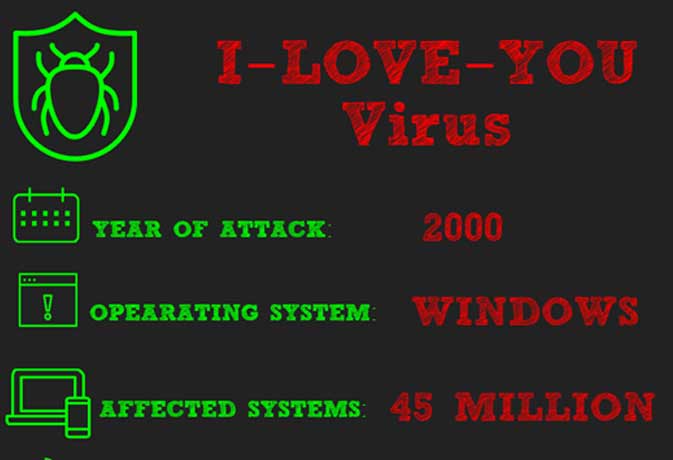



Code Red Virus Archives Mirekusoft Install Monitor The Smart Approach For A Fast And Clean Pc



1
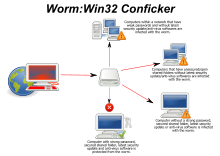



Computer Worm Wikipedia




10 Deadliest Computer Viruses Of All Time Hongkiat




The 15 Deadliest Computer Viruses




Amazon Com Mcafee Antivirus Protection 22 1 Pc Internet Security Software 1 Year Download Code Software




Amazon Com Mcafee Total Protection 22 3 Device Antivirus Internet Security Software Vpn Password Manager Dark Web Monitoring Included Pc Mac Android Ios 1 Year Subscription Download Code Software




Fix Red Screen Errors On Windows 10 11 Rsod Error
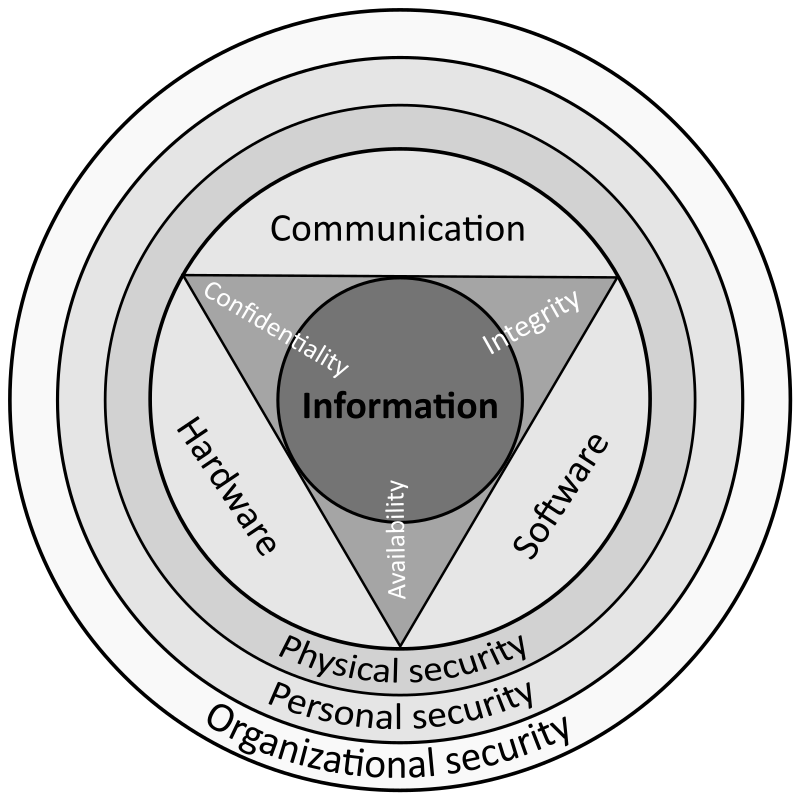



Malware Wikipedia




Top 10 Most Dangerous And Destructive Cyber Viruses Of All Time
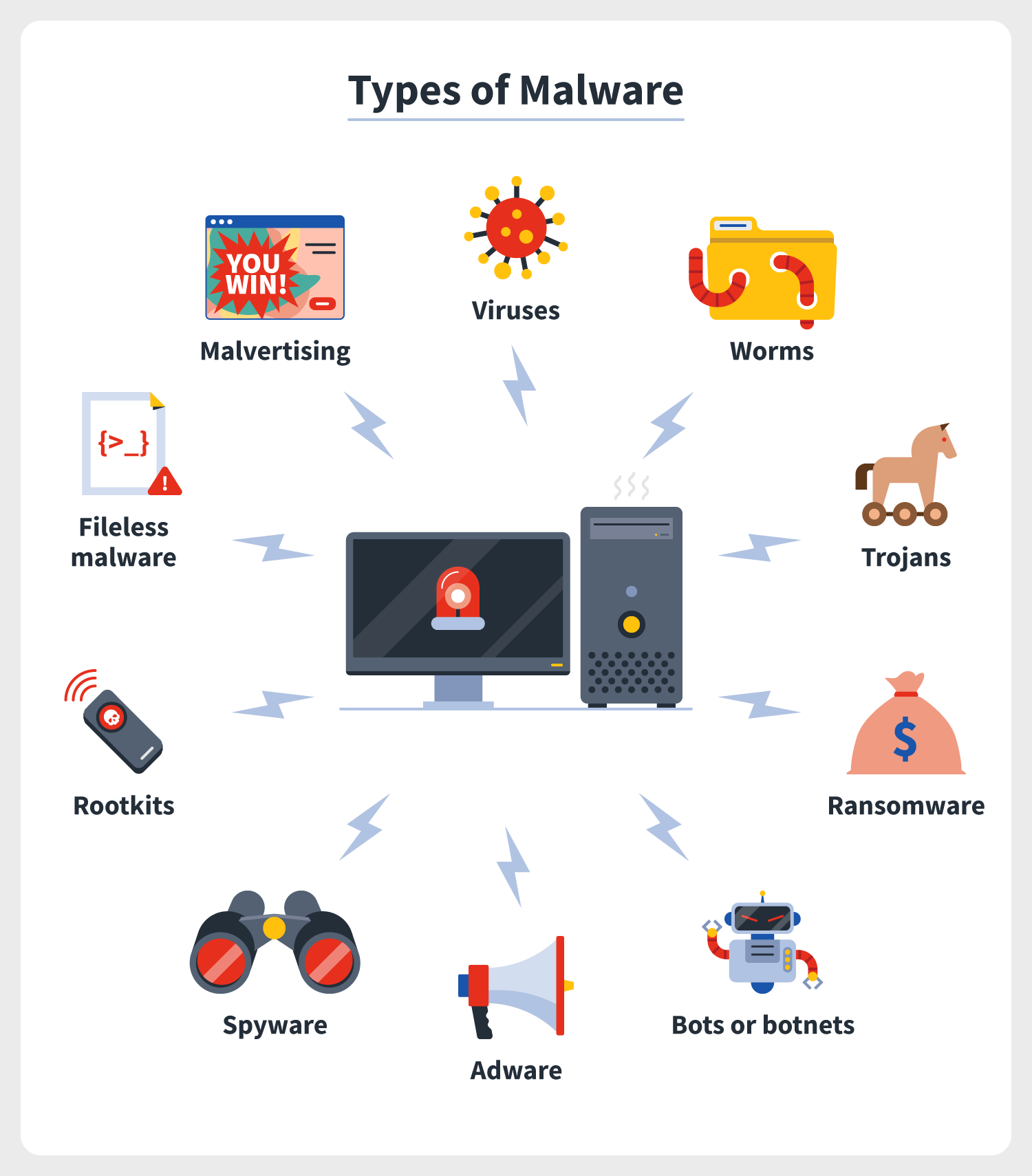



10 Types Of Malware How To Prevent Malware From The Start Norton



A Short History Of Computer Viruses




The Code Red Worm Hacking History Documentary Youtube




How Computer Viruses Work Howstuffworks




Cyber Threat Latest Computer Virus Malware Threats In 22




What S The Difference Between A Virus A Trojan A Worm And A Rootkit




Hackup S Virus Code In C




Low Code No Code Tools Are Everywhere Can They Deliver Protocol




10 Deadliest Computer Viruses Of All Time Hongkiat
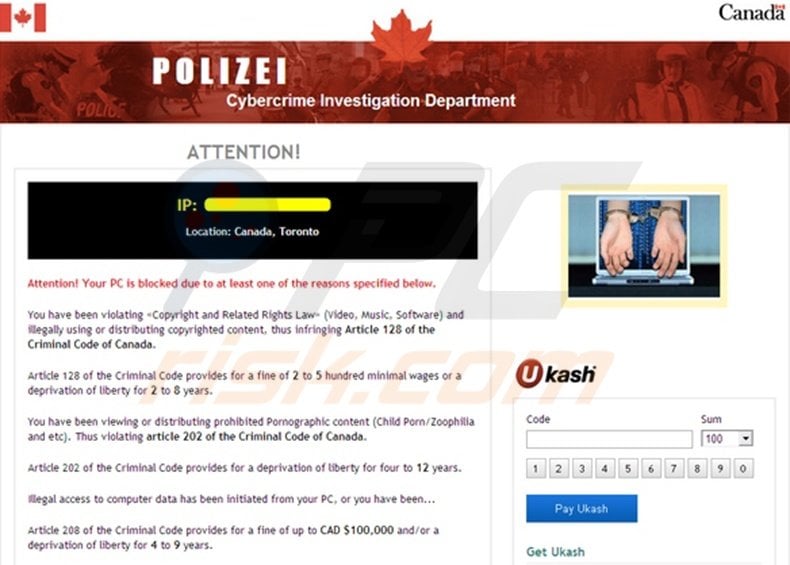



Polizei Virus Canada Decryption Removal And Lost Files Recovery Updated
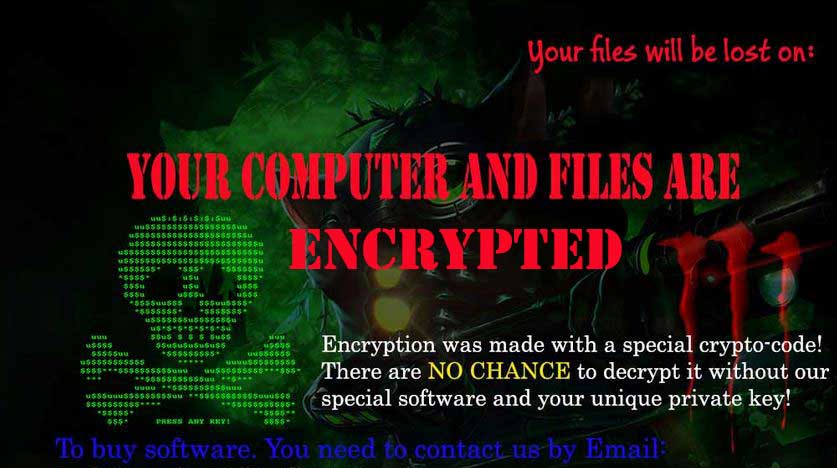



Bam File Virus Remove And Restore Encrypted Files How To Technology And Pc Security Forum Sensorstechforum Com




11 Malware Attacks That Nearly Wrecked The Internet




How To Create A Virus 9 Steps With Pictures Wikihow




The Functionality Of Encrypting Viruses By Ensar Seker Lotus Fruit Medium




10 Worst Computer Viruses Of All Time Howstuffworks
:max_bytes(150000):strip_icc()/how-to-tell-if-your-pc-has-a-virus-4590200-0-26a9bbbdc3d64c12950a58506fd9aaf7.jpg)



How To Tell If You Have A Computer Virus
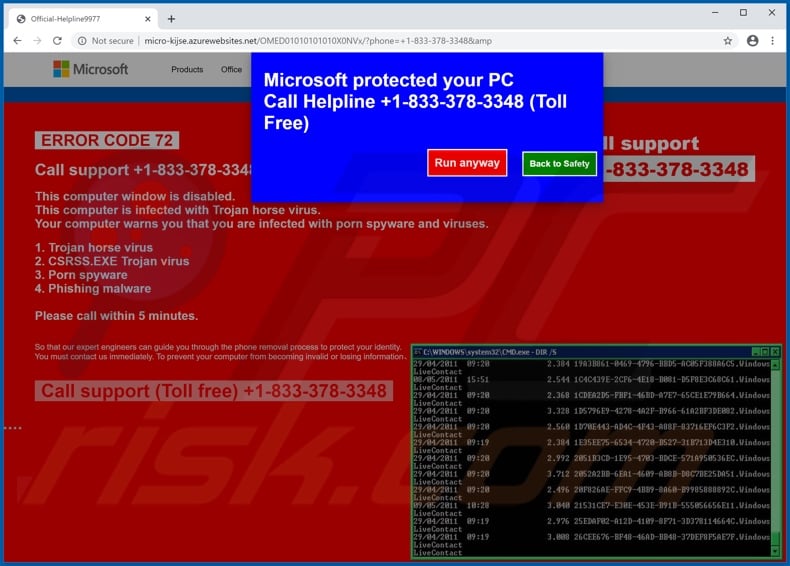



Error Code 72 Pop Up Scam Removal And Recovery Steps Updated



Codered The Virus Encyclopedia
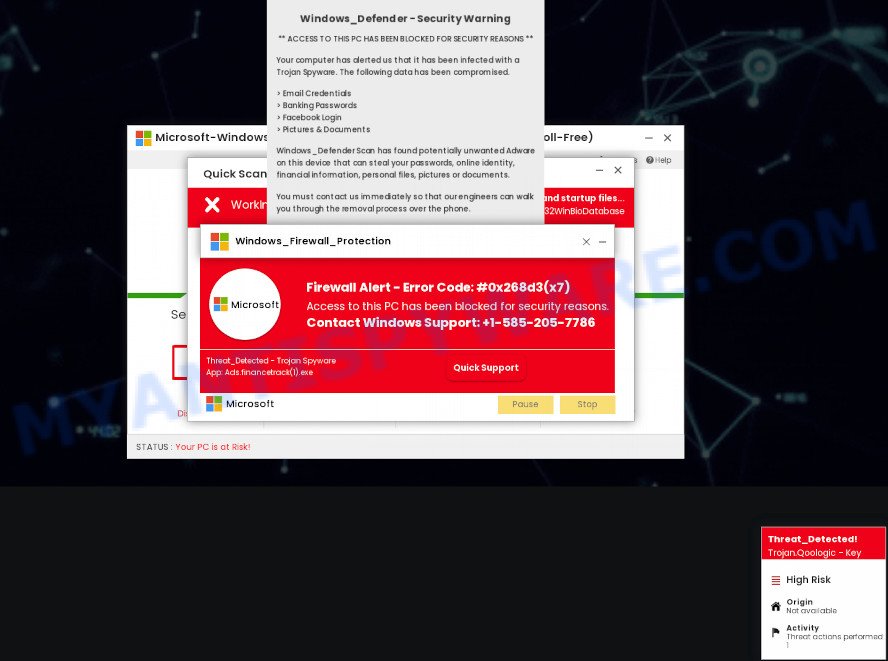



How To Remove Firewall Spyware Alert Pop Up Scam Virus Removal Guide



1




What Is A Computer Worm How Do You Prevent Them




Pc Tools Internet Security 10




Timeline Of The Worst Computer Viruses In History Hp Tech Takes




How To Get Rid Of A Computer Virus All You Need To Know




What Is Virus Code Red How To Remove Like




What Is Malware Everything You Need To Know About Viruses Trojans And Malicious Software Zdnet




Malware Names Microsoft Docs




Computer Virus Transfer Into Desktop Pc By Internet Lan Line Double Exposure Shot Of Backside Of A Computer And Red Binary Codes Hacker Virus Spywar Stock Photo Alamy




Pin On Best Online Deals India
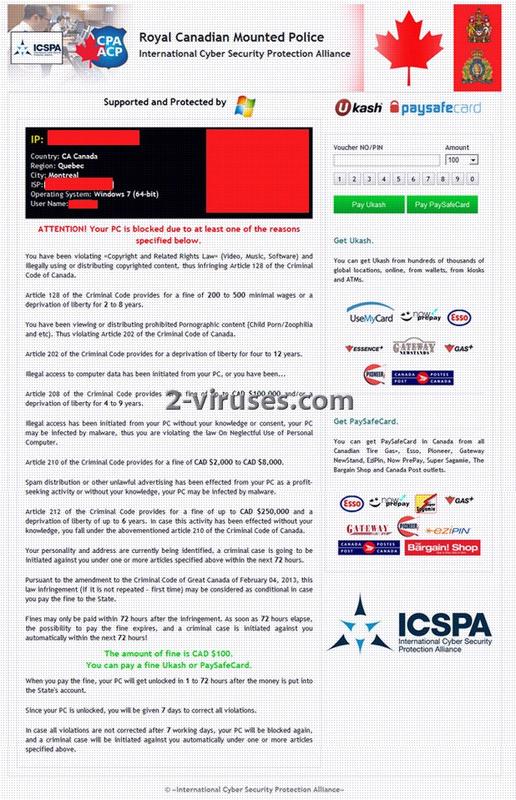



Royal Canadian Mounted Police Virus How To Remove Dedicated 2 Viruses Com




What Are Macro Viruses And How Do They Work




Master Penalty Document Virus Decryption Removal And Lost Files Recovery Updated



Find Virus On My Pc Stock Photo Crushpixel




The 10 Most Destructive Pc Viruses Of All Time Network Computing




What Is A Worm Virus Definition Examples Removal Tools Video Lesson Transcript Study Com
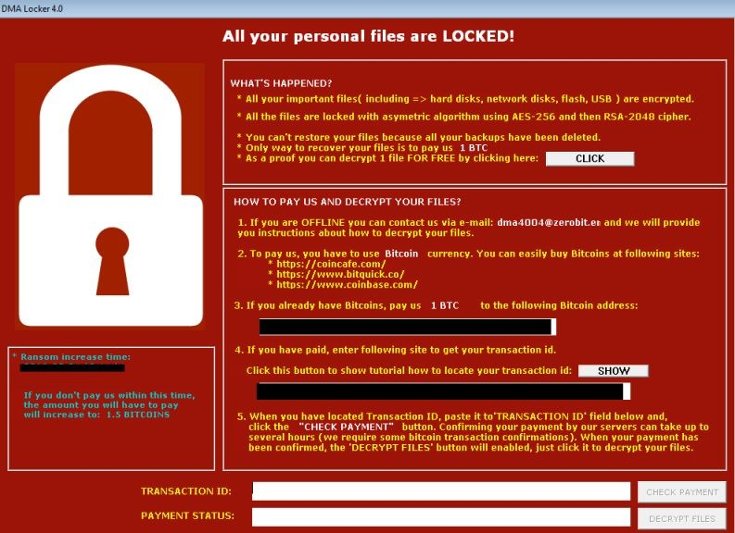



What Is Malware Malware Detection And Removal Imperva




Threat Report Reveals Pre Teen Children Developing Malicious Code Avg
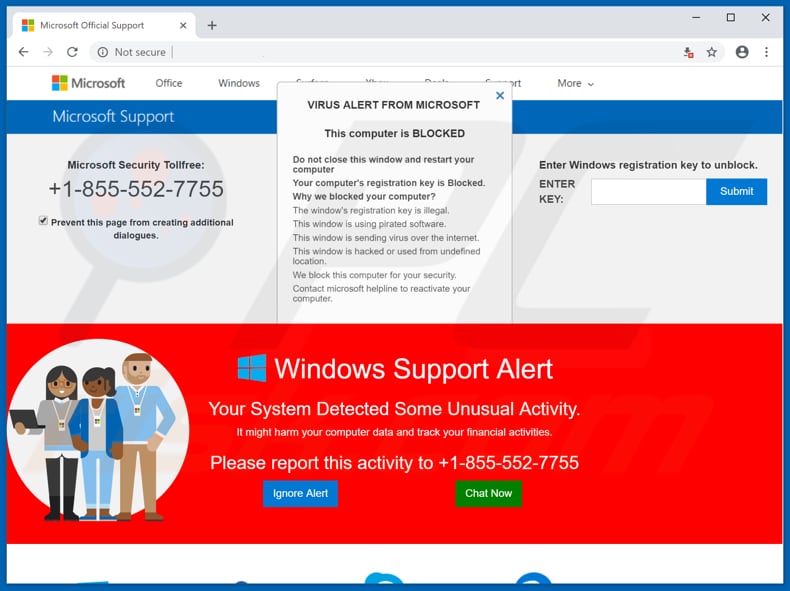



This Computer Is Blocked Pop Up Scam Removal And Recovery Steps Updated



0 件のコメント:
コメントを投稿